
In this blog post, we will explore both the benefits and risks of technology in commercial property. We will also offer insights on how companies can strike a balance between utilising technology and mitigating its potential risks. Finally, we will discover why IT network monitoring is an essential component of cybersecurity strategy.
Technology transforms commercial real estate
The widespread adoption of technology has revolutionised the way commercial real estate operates, bringing about both benefits and risks. On one hand, technology has enabled companies to streamline processes, increase efficiency, and reach new audiences. On the other hand, the increased reliance on technology has created new vulnerabilities, such as data breaches, cyber-attacks, and disruptions to critical systems.
Originally launched in 1985, Microsoft Excel might finally be losing its grip as the go-to application for property management. Proptech (property technology) has dramatically transformed the commercial real estate (CRE) industry over the past decade. From property search and leasing to management and construction, technology has improved efficiency, reduced costs, and made data-driven decisions possible.
Property search and leasing
Prospective tenants no longer need to visit properties in person or sift through stacks of paper. Today, they can search for properties online and take virtual tours from anywhere, saving valuable time. Online platforms like NovaLoca and LoopNet make it easy for tenants to search for properties based on location, square footage, and rental rate. They can compare multiple properties, and even get a feel for the surrounding neighbourhood through satellite images and street views.
Landlords and property managers also benefit from technology in the leasing process. Electronic signatures and document management systems streamline data collection, storage, and access, reducing the risk of misplacing important documents.
Property management
Property management firms have profited from technology. Mobile apps and cloud-based software offer convenience to property managers. They allow property managers to access real-time data and manage various aspects of their properties remotely, such as maintenance requests, budgets, and expenses. With these tools, property managers can carry out their duties from anywhere.
Property management software like Yardi and RealPage offer tools for work order tracking, maintenance scheduling, tenancy renewals, and rent collections. Building automation systems (BAS) can remotely monitor and control HVAC systems, lighting, and other building systems, saving time and reducing energy costs.
Construction
Technology has benefited the construction industry. Architects, engineers, and contractors use building information modelling (BIM) software for construction planning purposes. With BIM, they can create digital blueprints of buildings and determine the most efficient construction methods. BIM also enables them to simulate construction scenarios and identify and resolve potential problems before construction starts.
The construction industry is using drones and unmanned aerial vehicles (UAVs) to conduct site surveys and building inspections. This technology can provide a bird’s-eye view of a construction site, allowing contractors to identify potential obstacles and adjust their plans before construction starts.
Investment
Finally, technology is changing the way CRE projects get financed. Several online platforms make it possible for anyone to invest in commercial property with just a few clicks. These platforms allow investors to diversify their portfolios, access new investment opportunities, and participate in commercial real estate without having to physically manage properties.
Big data analytics is also transforming the way investors approach commercial real estate. Investors can now access data on market trends, property performance, and economic indicators to make more insightful decisions about their investments. This data can also be used to create predictive models that help investors understand emerging market trends.
Commercial real estate must embrace cybersecurity
As commercial property businesses increasingly rely on proptech to improve their operations, the number of security threats and vulnerabilities expands proportionally. All too often, a widening gap grows between existing cybersecurity safeguards and the actual risks and vulnerabilities an organisation faces.
Sensitive data
One of the main reasons why cyber security is important in the CRE sector is because of the sensitive information that is stored and processed. Commercial property businesses often deal with confidential information such as tenant data, financial records, and sensitive legal documents. In case of a breach, this data can be stolen and used for malicious purposes, leading to serious consequences for the affected parties.
IoT
Forecasts predict that by 2027, commercial buildings will have 2.5 billion IoT (Internet of Things) connected devices installed.1 Real estate operations increasingly use these devices to help manage security, environment, and energy consumption. Despite their benefits, these devices also introduce new vulnerabilities that cybercriminals can exploit. For instance, a hacker could gain access to a building’s security system and unlock doors, potentially granting unauthorised access to the building.
Hundreds of IoT devices hacked
In 2021, a German building engineering firm reported a hacking incident that affected hundreds of their building automation system (BAS) devices, such as motion detectors, and shutter controls. The attacker purged the smart devices and reset passwords, denying the firm access. No ransom demand was made, and the motive for the attack remains unclear.2
Costs of failure
Cyber-attacks can have a significant financial impact on commercial property businesses. The costs of a cyber breach include identifying and fixing the source of the problem, repairing any damage done to the network, notifying customers and partners, and trying to restore the reputation of the business. Additionally, a breach can lead to legal action, regulatory censure, and hefty fines.
Common risks and vulnerabilities
Unfortunately, many commercial landlords and managing agents lack an understanding of the security risks posed by unsupported IT equipment, IT licensing requirements, and unauthorised third-party apps connected to a building’s network. Neglecting these risks could result in an unplanned building shutdown, negative publicity, disgruntled tenants, and lost revenue.
Unsupported IT equipment
Running outdated hardware and software makes an organisation more vulnerable to viruses, malware, and ransomware. The failure of unsupported network equipment can close a commercial property for days.
Out-of-license IT equipment
Network equipment can stop working if annual licenses are not renewed. This can result in a partial or complete network failure and impromptu closure of the affected building.
Unauthorised third-party apps
Having unauthorised apps connected to a building’s computer network can result in several negative outcomes. These include poor network performance, unexpected downtime, data breaches, and even the sabotage of critical systems.
Unauthorised network devices are any devices that are connected to an organisation’s network without proper authorisation or approval from the network administrator. These devices can include personal devices such as laptops, smartphones, and tablets, as well as internet of things (IoT) devices such as smart speakers and security cameras.
Unauthorised network devices can pose a significant cyber security risk to organisations for several reasons:
- Lack of security: Personal devices and IoT devices often lack the same level of security protection as the organisation’s own devices, making them vulnerable to cyber-attacks.
- Unpatched software: Unauthorised devices may run outdated or unpatched software, which can also make them vulnerable to cyber-attacks.
- Unsecured networks: Personal devices may be connected to unsecured networks, which can also pose a risk to the organisation’s network if they are connected to the same network.
- Rogue access points: Unauthorised network devices can also act as rogue access points, allowing attackers to bypass network security measures and gain unauthorised access to sensitive information.
- Data breaches: Unauthorised network devices can also be used to steal sensitive data or to spread malware within the organisation’s network.
Therefore, it’s important for organisations to implement proper security measures, such as device authentication and network segmentation, to limit the risk posed by unauthorised network devices.
Three steps towards better security
Commercial property firms must take proactive measures to ensure their cyber security.
The first step is to conduct a thorough risk assessment to identify potential threats and vulnerabilities. This should involve examining the organisation’s information security systems and processes, as well as conducting regular penetration testing and vulnerability scans.
The second step is that CRE firms implement strong security protocols and controls, such as firewalls, encryption, and multi-factor authentication (MFA). Additionally, it is crucial to have a robust disaster recovery plan in place, so that the business can quickly respond and recover from a breach. This should include regular backups of critical data and systems, as well as regular testing of the disaster recovery plan.
The third step for commercial real estate businesses involves providing regular training to employees on cybersecurity best practices. This training should focus on recognising and avoiding phishing scams and maintaining strong passwords. By providing this training, all members of the organisation will be better aware of the risks and how to prevent them.
Lastly, it is important to work with a trusted third-party cyber security provider to help manage cyber security risks. This can include managed security services, network monitoring, and security consulting. These services can enhance the security of an organisation’s systems and data. They also provide the necessary expertise and resources for a quick response to any security incidents.
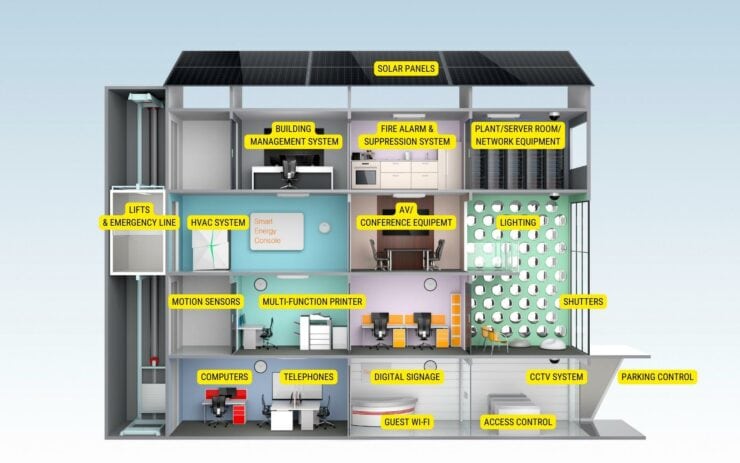
The importance of network monitoring
As we have seen, commercial property companies have become increasingly reliant on technology to improve their operations and provide better services to tenants. However, with this increased reliance on technology comes a corresponding increase in security risks. Cybersecurity threats are becoming more sophisticated and frequent, making it crucial for commercial real estate businesses to take proactive measures to ensure their IT network is secure. One of the most important steps in securing a network is to implement continuous monitoring.
IT network monitoring is the process of continuously checking a network for potential security threats, performance issues, and other anomalies. It helps to identify potential problems early before they become critical and enables the prompt resolution of any issues that do arise. Network monitoring is an essential component of a comprehensive cybersecurity strategy for commercial properties.
Three BIG benefits of network monitoring
Security
IT network monitoring boosts security through constant surveillance. It detects potential security threats, alerts tech support, and enables them to act before harm occurs. For instance, if an unauthorised user attempts to access the network, network monitoring detects the attempt, alerts the IT team, and helps them prevent sensitive information from being accessed. IT network monitoring also detects malware, viruses, and malicious software, preventing harm to the network.
When things go wrong
The following examples illustrate the consequences of failing to monitor and manage a network properly. These consequences can be dire.
Google HQ Hack
In 2013, two researchers successfully hacked the building management system (BMS) of Google’s corporate HQ in Sydney, Australia. Although a security patch was available for a known vulnerability within the BMS, it had not been implemented due to a lack of network management.3
Equifax Data Breach
In 2017, Equifax, one of the world’s largest credit reporting agencies, suffered a data breach that impacted the personal information of 150 million people. The breach was caused by a vulnerability in Equifax’s web application software, which was not being monitored for security.4
Capital One Data Breach
In 2019, Capital One suffered a data breach that exposed the personal information of approximately one hundred million customers. An unmonitored, misconfigured firewall caused the breach. As a result of the breach, Capital One paid a fine of £66 million. The company also settled customer lawsuits for around £157.5 million.5
Network performance
IT network monitoring helps improve the performance of a network in several ways:
- Identifying bottlenecks: IT network monitoring tools can detect bottlenecks in network performance, such as slow response times or high utilisation levels on specific devices. This information can help network administrators identify the cause of the issue and take steps to resolve it, improving overall network performance.
- Detecting network outages: IT network monitoring can also detect network outages and other disruptions, allowing administrators to quickly respond and resolve the issue, minimising downtime and preserving network availability.
- Improving network utilisation: IT network monitoring can also help network administrators optimise network utilisation, by providing detailed information about network usage patterns, resource utilisation, and application performance. This information can be used to make informed decisions about network capacity planning and infrastructure upgrades, helping to improve overall network performance.
Compliance
IT network monitoring not only improves security, performance, and uptime but also helps CRE businesses comply with regulations and standards. Paid parking systems, for instance, must follow the Payment Card Industry Data Security Standard (PCI DSS) which requires network monitoring. Implementing network monitoring helps commercial landlords and managing agents comply with regulations while reducing legal and financial risks.
Network monitoring options
IT network monitoring offers several options, including on-premise solutions, cloud-based solutions, and managed services. On-premise solutions, installed on the local network, offer detailed monitoring and reporting. Cloud-based solutions, hosted in the cloud, allow remote access to network monitoring data. Managed services provide commercial property firms with expert IT support and monitoring, eliminating the need for in-house IT staff.
In conclusion
The commercial property sector increasingly relies on technology to achieve business efficiencies. Technology is also helping the sector to meet its environmental, social and governance (ESG) responsibilities. However, this means CRE businesses are more exposed to cyber threats. Consequently, they must take proportional safeguards to reduce risks.
IT network monitoring improves security, performance, and compliance. It does this by continuously checking the network for potential threats, performance issues, and anomalies. By partnering with a trusted IT provider, commercial property firms can implement a solution that meets their specific needs, secures their networks, and safeguards sensitive data.
Modern Networks is the UK’s leading provider of IT-managed services to the commercial property sector.
Contact us today for a comprehensive cyber security review, and to learn more about the value of networking monitoring. Alternatively, visit our IT support pages for more information.
Sources: